Configuring Active Directory as the Authentication Provider (OBIEE 11.1.1.9)
Purpose:
Connecting the OBIEE WebLogic LDAP server to Microsoft Active Directory, so users can log-into the dashboard using their Windows Active Directory username and password, and retrieve group membership.
Whilst OBIEE comes with the embedded WebLogic LDAP server to hold users and groups, the license for this is restricted such that you can't just move all users from other applications into the LDAP server.
If you search in the internet and Oracle docs for instructions on how to integrate OBIEE 11g with Active Directory, there are many different ways to do it with set of instructions.
A lot of this is because Active Directory is highly-configurable, and a lot depends on how much you want to replace, or just work alongside, the existing WLS LDAP server.
Our objective is to keep the WLS LDAP server and the user accounts within it and then make it possible for Active Directory users also log in and be assigned to the standard application roles that the WLS LDAP users have.
Procedure:
This procedure illustrates how to configure Oracle Business Intelligence to use Active Directory.
Before starting the configuration, we need the following Active Director users and groups as below.
ADbiapps, will be used as the principal that OBIEE uses to connect to the Active Directory server
ADBISystemUser a user on Active Directory who wants to have administration rights in the Presentation Server and BI Server
Above users are organized into three groups in the AD server:
ADBIAdministrators, analogous to the BIAdministrators group in the WLS LDAP server
ADBIAuthors, analogous to the BIAuthors group in the WLS LDAP server
ADBIConsumers, analogous to the BIConsumers group in the WLS LDAP server
The groups have just got those users as members, and the users are just regular AD users, including the ADBISystemUser account.
Let's go into the WebLogic Server Administration Console http://[machine_name]:7001/console) and start configuring the system for Active Directory integration.
To configure Active Directory as the Authentication Provider:
- Log in to Oracle WebLogic Server Administration Console, and click Lock & Edit in the Change Center.
- Select Security Realms from the left pane and click myrealm.
The default Security Realm is named myrealm.
- Display the Providers tab, then display the Authentication sub-tab.
- Click New to launch the Create a New Authentication Provider page.
- Enter values in the Create a New Authentication Provider page as follows:
- Name: Enter a name for the authentication provider. For example, ADAuthenticator.
- Type: Select ActiveDirectoryAuthenticator from the list.
- Click OK to save the changes and display the authentication providers list updated with the new authentication provider.
- Now click on this new authentication provider in the list, and then when the Settings for ADProvider page is shown, set the Control Flag to SUFFICIENT, and press Save.
- Click DefaultAuthenticator in the Name column to display the Settings page.
- In the Common Authentication Provider Settings page, change the Control Flag from REQUIRED to SUFFICIENT and click Save.
Then, again click on Providers and with the list of authentication providers displayed, press the Reorder button.
Change the order of the providers so that MSADProvider is first, followed by DefaultAuthenticator, DefaultIdentityAsserter and TrustServiceIdAsserter
Click ok.
With the list of authentication providers displayed Click on MSADProvider
Click on the Provider Specific tab
Enter the following details for your Active Directory installation, amending the settings as appropriate for your AD server.
Provider Specific |
Connection |
|
Host: | 10.10.2.76 |
Port: | 389 |
Principal: | CN=ADbiapps,DC=GLC,DC=COM,DC=SA |
Credential: |
|
Confirm Credential: |
|
Users |
|
User Base DN: | DC=GLC,DC=COM,DC=SA |
User From Name Filter: | (&(sAMAccountName=%u)(objectclass=user)) |
User Name Attribute: | sAMAccountName |
Groups |
|
Group Base DN: | DC=GLC,DC=COM,DC=SA |
Group From Name Filter: | (&(sAMAccountName=%g)(objectclass=group)) |
Static Groups |
|
Static Group Name Attribute: | sAMAccountName |
Click Save.
In the Change Center, click Activate Changes.
Restart Oracle WebLogic Server.
Once complete, log in again into the WebLogic Admin Console and select Security Realms > myrealm > Users and Groups. You should then see the Active Directory users listed alongside the WLS LDAP ones.
Next we will switch over to Enterprise Manager, first to configure Fusion Middleware's Oracle Platform Security Services to accept users and groups from both WLS LDAP and Active Directory when logging into the dashboard, and then we'll map the Active Directory groups to their equivalent application roles.
Log into Enterprise Manager, and select the WebLogic Domain > bifoundation_domain menu item on the left. Right-click on it and select Security> Security Provider Configuration. When the Security Provider Configurationpage is displayed, expand the Identity Store Provider area and press the Configure… button.
The Identity Store Configuration page will then be displayed. Press the Add button next to the Custom Properties area, and add a new custom property with these settings :
Property Name : virtualize
Value : true
Press OK to close the page.
Update the system.user key points to an existing user BISystemUser in Active Directory, then the system.user Credential Key will have be updated from Enterprise manager Credential Store (to point to the correct user/password
Edit Key > Select map= oracle.bi.system
Key = system.user
TYpe = Password
User name = this should be your AD user
Password= password for AD user
Now right-click on the Business Intelligence > coreapplication entry in the left-hand side menu, and select Security > Application Roles. As you may have done with the application role settings in yesterday's postings, edit the BIAdministrator, BIAuthor and BIConsumer application roles so that the new Active Directory groups are listed as members.
Doing this ensures that the Active Directory users get the same type of Presentation Server and repository privileges as WLS LDAP users, but they won't have administration access to WebLogic or Enterprise Manager.
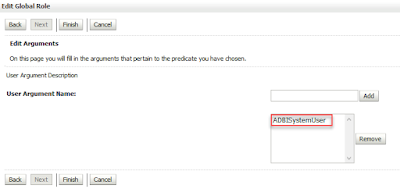
Add AD User ADBISystemUser are mapped to Application Roles
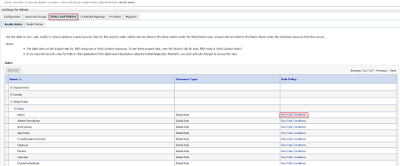
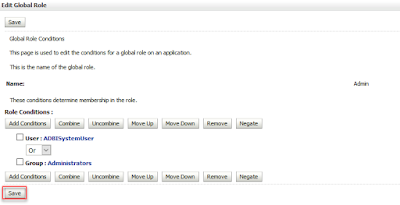
Log in to Weblogic Admin console > Security Realms from the left-hand menu > drill on your security realm in the main screen (e.g. myrealm)
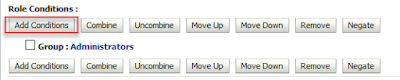
> Roles and Policies Tab >expand Global Roles> then Roles, then click on the link marked View Role Conditions
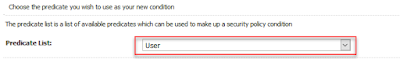
For the OBIEE application role eg "Apptester" you should see the corresponding AD group in View Role Conditions eg Group=Apptester (created on AD)
· Doing this ensures that the Active Directory users get the same type of Presentation Server and repository privileges as WLS LDAP users, but they won't have administration access to WebLogic or Enterprise Manager.
You can, if you want, grant these users the same sorts of domain administrator rights as the WLS LDAP users, and you can indeed remove all of the WLS LDAP users and groups and move over to Active Directory entirely. But in most cases I see, this level of integration is sufficient, as it still allows the OBIEE administrators to control their own user accounts and privileges.
· You should now be able to log in as one of the Active Directory users. In the screenshot below, the AD User user has logged in, and has been granted the BIAuthor role through their membership of the ADBIAuthors Active Directory group. If Anne Administrator, an Active Directory user assigned to the ADBIAdministrator group, logs in she will be able to administer the Presentation Server permissions and privileges, but she won't be able to log into Enterprise Manager to change the repository, for example.
Useful Links and Oracle Doc ID’s
After Upgrade from OBIEE 10g Unable To Login To OBIEE 11g : "Unable to find user in identity store" (Doc ID 1482788.1)
OBIEE 11g: Alert: Users Unable to Log in to OBIEE 11.1.1.9 if Using MSAD or Other Third-Party LDAP as the Identity Store and Virtualization is Set to true. (Doc ID 2016571.1)
OBIEE 11g: How To Setup ADSI LDAP Security Provider (Doc ID 1273961.1)
https://www.rittmanmead.com/blog/2010/11/oracle-bi-ee-11g-security-integration-with-microsoft-active-directory/
https://www.rittmanmead.com/blog/2010/11/oracle-bi-ee-11g-security-integration-with-microsoft-active-directory/
http://paulcannon-bi.blogspot.com/2012/07/configuring-ldap-authentication-for.html
https://docs.oracle.com/middleware/11119/biee/BIESC/privileges.htm#BABBCEFH
https://www.rittmanmead.com/blog/2012/03/obiee-11g-security-week-connecting-to-active-directory-and-obtaining-group-membership-from-database-tables

































